Are you already using ReCon? If so, check out the ReCon Monitoring and Configuration page.
Why run ReCon?
Have you ever wondered who or what is tracking you and/or stealing your personal information?
Unfortunately, your mobile devices currently give you
little or no way to tell if this is the case. Even if they did, they don't give you
any way to control it except to decline to install an app. With ReCon,
we give you a way to see how your personal information is transmitted to other
parties, and allow you to block or modify it with fine granularity. A demo is shown in the video and you can learn more details in this tutorial.
What does ReCon do?
ReCon analyzes your network traffic to tell if personal information is being transmitted, and it doesn't even need to know what is your personal information to work. It detects device/user identifiers used in tracking, geolocation leaks, unsafe password transmissions, and personal information such as name, address, gender, and relationship status. We make this information available to you via a private Web page, and allow you to tell us if we found important leaks, and whether we should block or modify them. Check out our services page to get more details.
Click here to see what popular apps are leaking about our users, and join today (using the button below) to find out what your apps are leaking.
For more details about our methodology, please check out our technical details page, written both for non-technical and technical audiences.
How do I start?
ReCon currently works for iOS and Android (4.0+). It is beta software, so there are some limitations and we appreciate your patience and help with fixing them. To install, follow this links on the sidebar.
To reserve a spot on the waiting list, you need to first signup for an IRB approved study. You will be be redirected to the signup form after passing this captcha test.
Screen shots
-
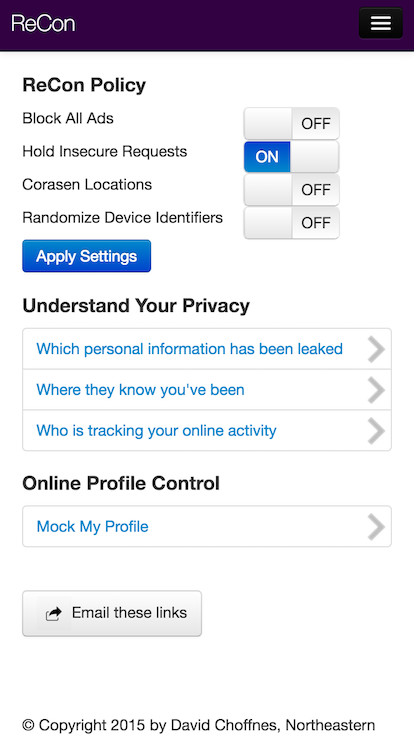
Configuration page
-
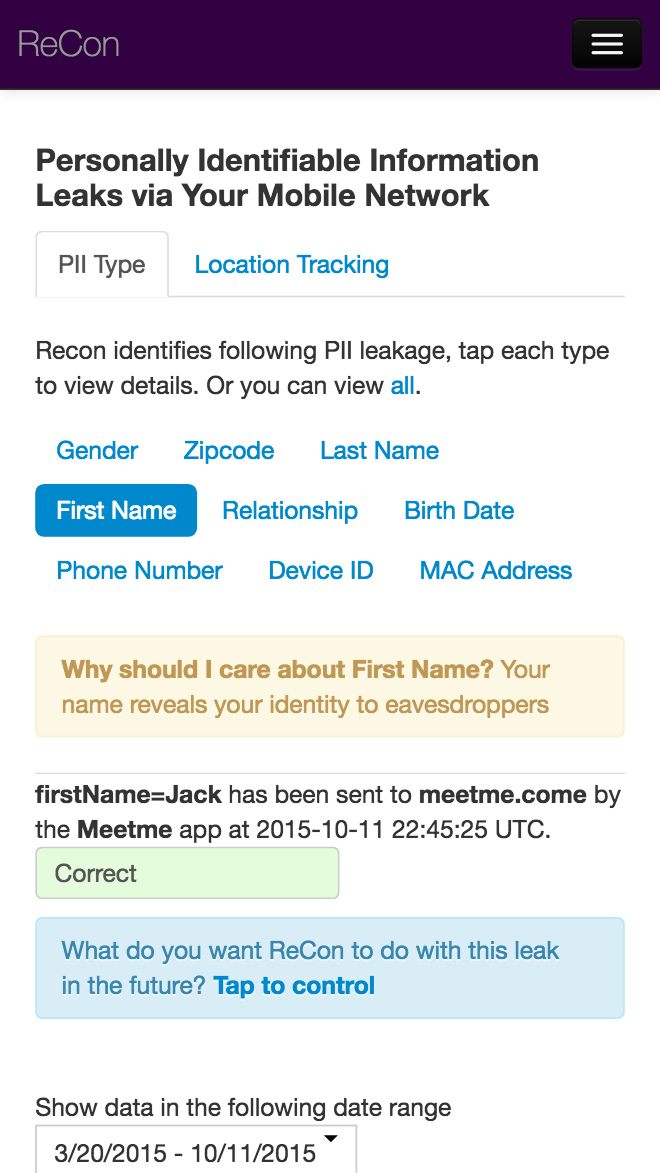
Review privacy leaks
-
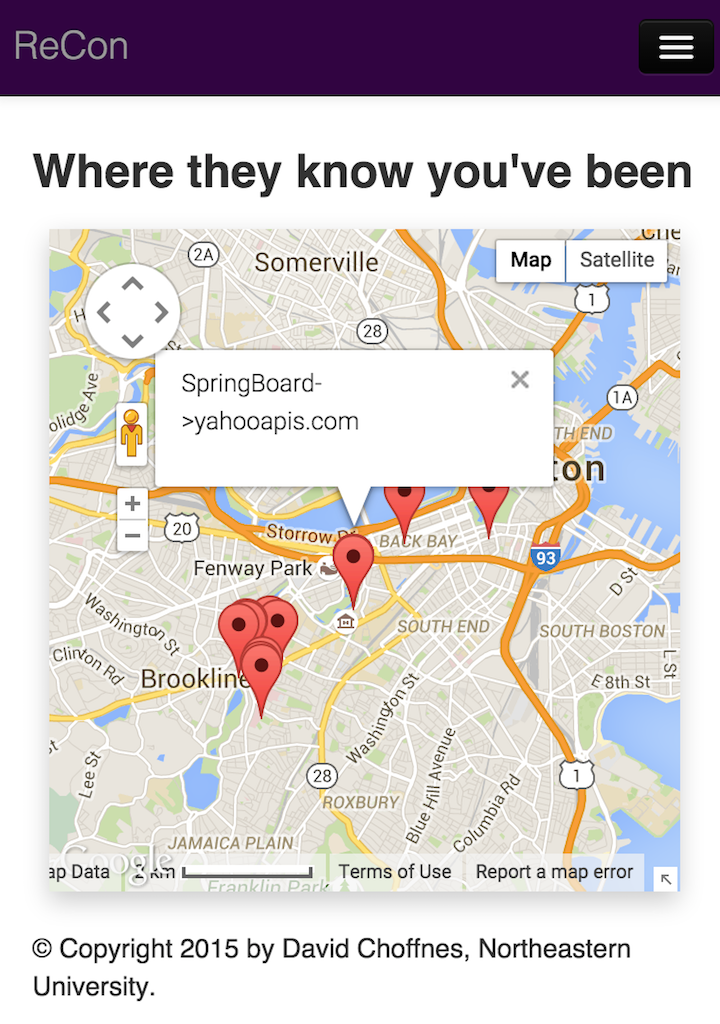
Review location leaks
-
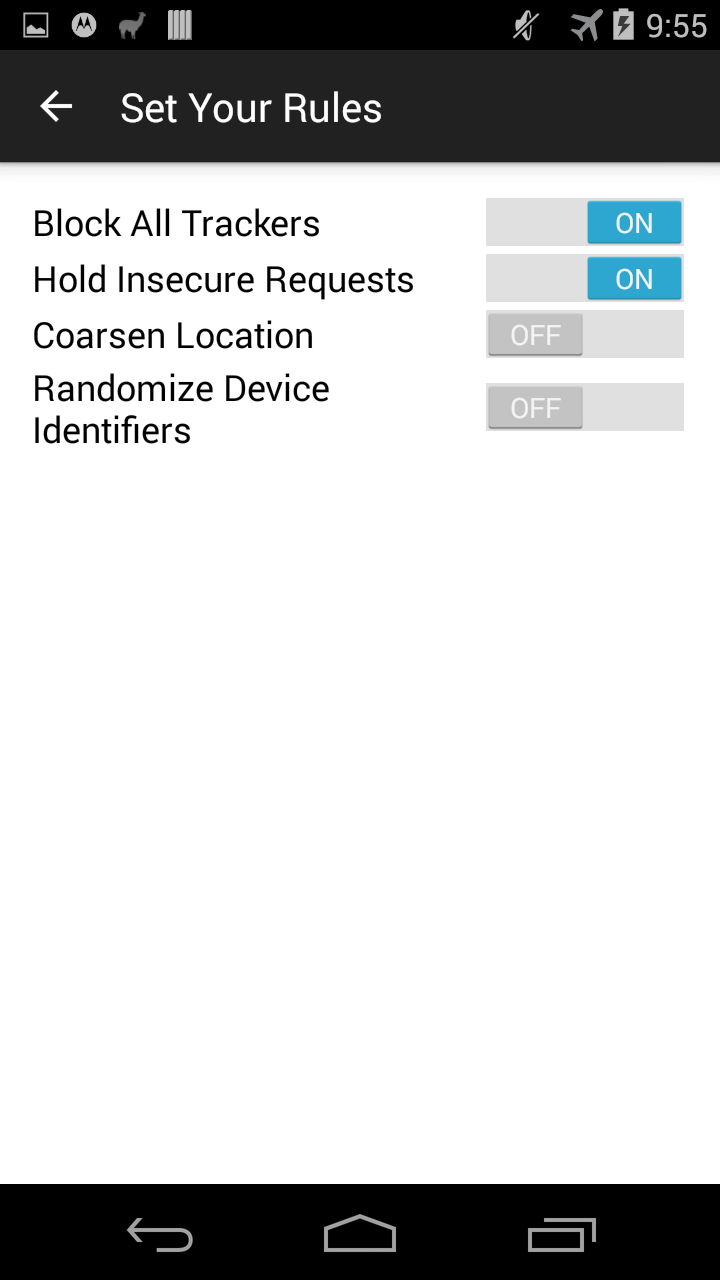
Set general rules
-
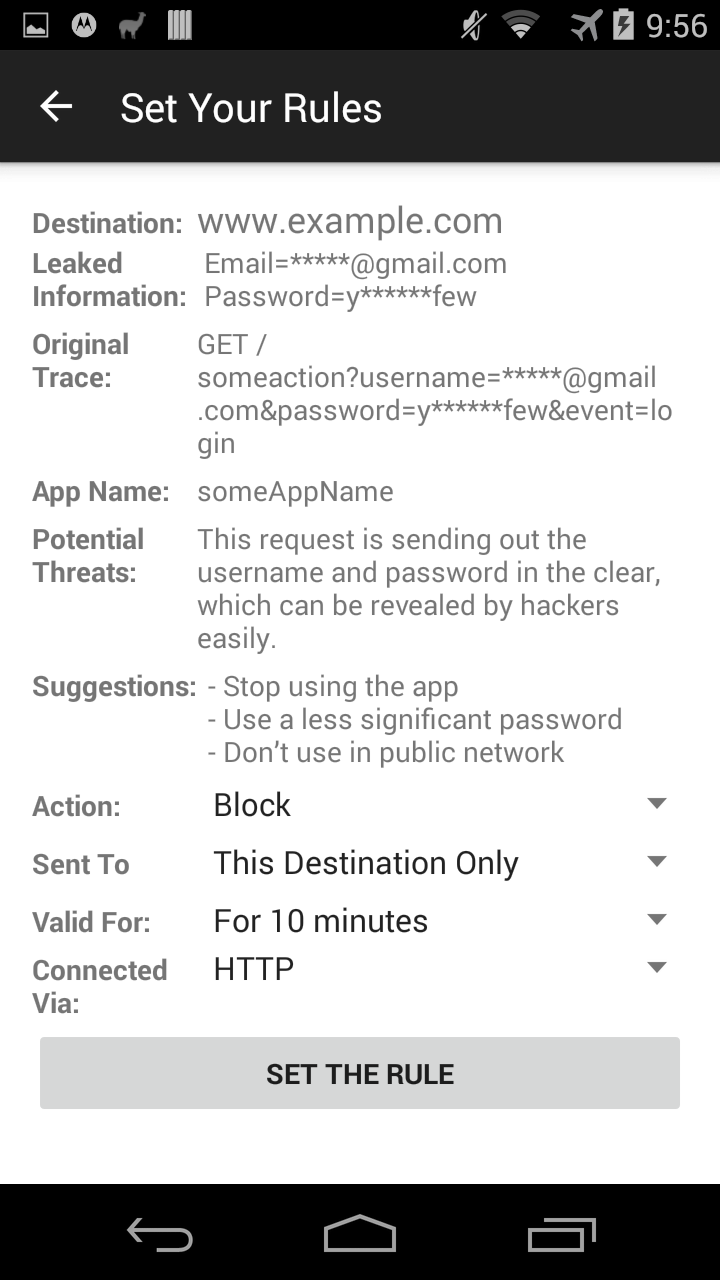
Set detailed rules
-
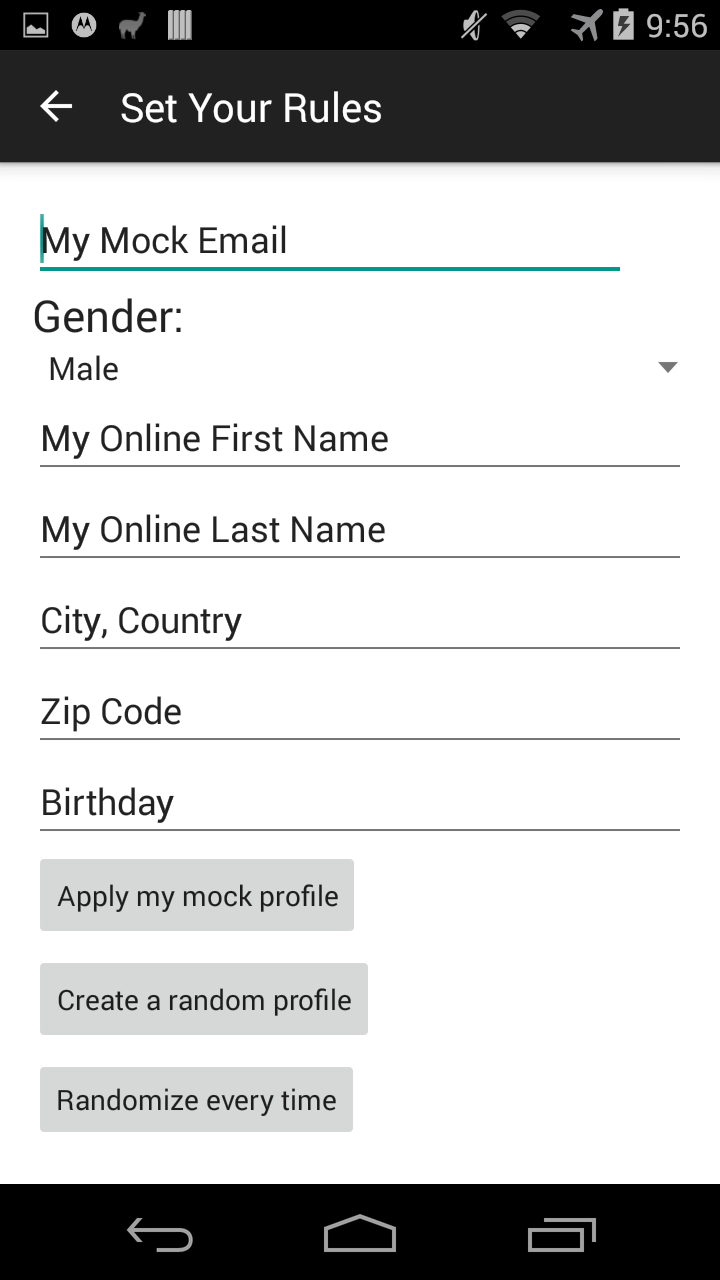
Mock your profile